NERC's New INSM Regulation: Assessing Impact and Ambiguity
By Patrick Miller
The recent draft release of NERC's new CIP Standard for Internal Network Security Monitoring (INSM) sparks a conversation filled with anticipation and skepticism. With directives from FERC Order 887 echoing in its language, the draft attempts to navigate through the challenges of creating a new regulation to address situations where vendors or individuals with authorized access are considered secure and trustworthy but could still introduce a cybersecurity risk.
On December 14, NERC released the first draft of the new Internal Network Security Monitoring (INSM) language for CIP-007-X. This addition to the NERC CIP standards was directed by FERC on January 19th through Order 887. FERC directed NERC to draft regulation that would…
“require internal network security monitoring (INSM) for CIP-networked environments for all high impact bulk electric system (BES) Cyber Systems with and without external routable connectivity and medium impact BES Cyber Systems with external routable connectivity.”
We’ve waited almost a year for the drafting team to provide the new language for industry comment. What did we get?
Confusion.
In short, there is a new Requirement 6 added to CIP-007. It essentially repeats the language from the FERC Order, with some notable areas that are bound to create friction.
Let’s begin.
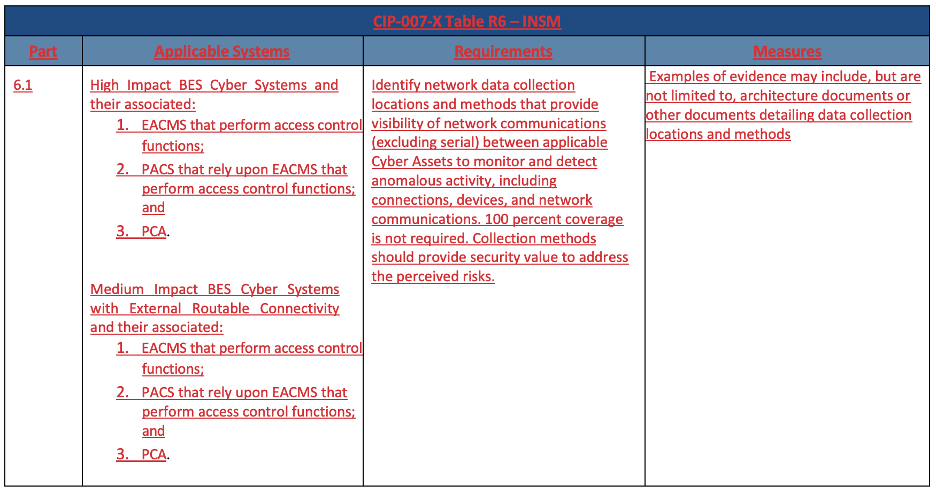
CIP-007-X Part 6.1
For the first subrequirement (part 6.1, above), identification of “network data collection locations and methods that provide visibility of network communications between applicable Cyber Assets to monitor and detect anomalous network activity” is required. What qualifies as sufficient visibility? Do I need to use an anomaly detection platform or will firewall, router, and switch logs work? Anomalous network activity can mean different things to different people. How often do I need to monitor? Will once a year work?
On we go. Serial is excluded, no surprises. But then, in what is easily the most interesting choice in regulatory language since “Identify, Assess, and Correct,” it states that 100% coverage is not required.
So how much coverage is required? Well, enough to “provide security value to address the perceived risks.” What is security value and how is it measured? What if I don’t perceive any risks? Am I allowed to do 1% coverage, for the value I want (none), to cover the risks I’m not interested in knowing? This language is not auditable. If FERC allows this, many will lose some costly bets.
Before we go on to the next requirement, notice that EACMS that perform access control functions are included in the Applicable Systems column. This one has confused many, since it goes beyond what the FERC Order requested, and beyond the generally understood (but also not defined as part of this effort) definition of Internal Network Security Monitoring. Most importantly, the internal part. EACMS generally (but not always) control and monitor access to/through the Electronic Security Perimeter (ESP). Does this mean we are expected to monitor those EACMS that are external to the ESP?
On to the second subrequirement (part 6.2, below). This one requires the entity to log collected data regarding network communications at the network locations identified above in part 6.1. This one makes sense, and should survive fairly comment-free.
CIP-007-X Part 6.2
On to the third subrequirement (part 6.3, below). Here the entity is required to evaluate the collected data to document the expected network communication baseline. The drafting team does not define the elements of a network baseline. Is this simply IP talks to other IP? Is it IP talks to other IP on this port/protocol? Usually during these time windows, with these accounts/users? Without any clarification, assume it just means the minimum necessary to define network communication (routable IPs).
CIP-007-X Part 6.3
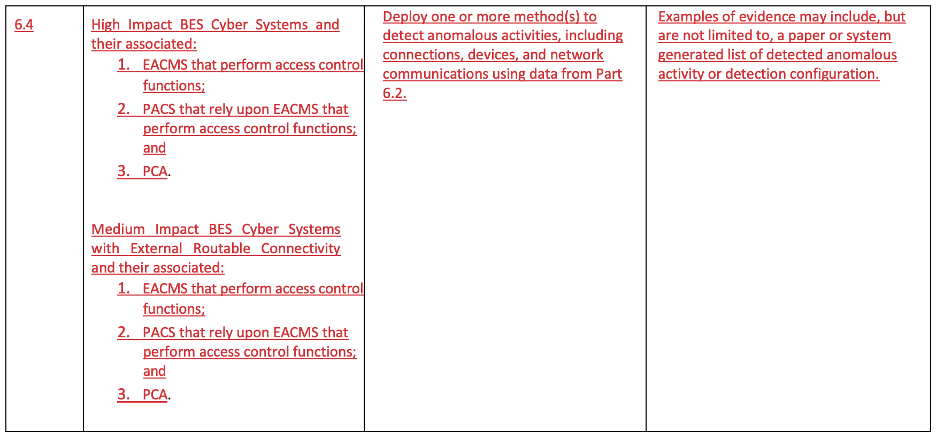
Let’s go to the fourth subrequirement (part 6.4, below). The entity is required to “deploy one or more method(s) to detect anomalous activities, including connections, devices, and network communications using data from part 6.2.” We still don’t have any additional clarity on what anomalous means. Is it anything that deviates from the baseline? If so, what are the minimum attributes that qualify for a baseline?
CIP-007-X Part 6.4
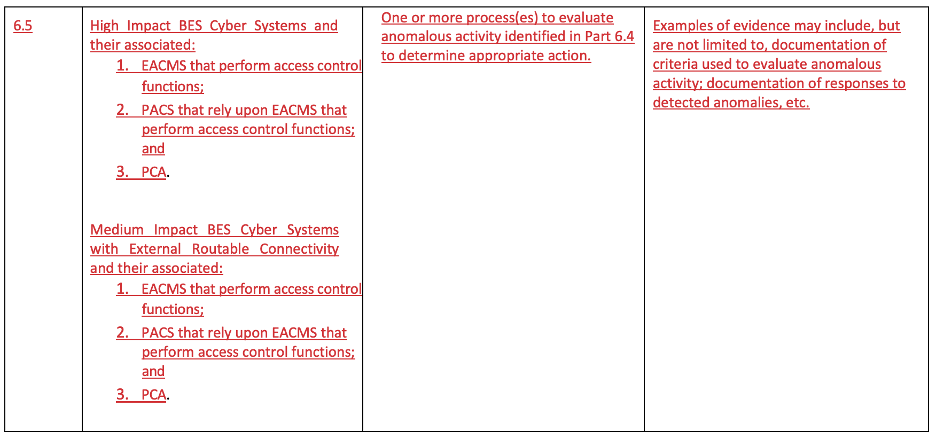
For the fifth subrequirement (part 6.5, below), the entity is required to “have one or more process(es) to evaluate anomalous activity identified in 6.4 to determine appropriate action.” We still don’t know what qualifies as anomalous, but we are expected to identify it and determine appropriate action. My appropriate action could be to log it and get back to work. Note that it also doesn’t include any hooks into CIP-008 incident response.
CIP-007-X Part 6.5
Subrequirement six (part 6.6, below) requires the entity to “Develop one or more method(s) to retain network communications data and other relevant data collected with sufficient detail and duration to support the investigation of anomalous activity.” We don’t have a definition of anomaly, so it may be challenging to determine what is sufficient detail. The duration isn’t specified, but the norm is 90 days from similar areas within other standards/requirements. Also note that the investigation part isn’t required. Just that you need to have sufficient detail to do so.
CIP-007-X Part 6.6
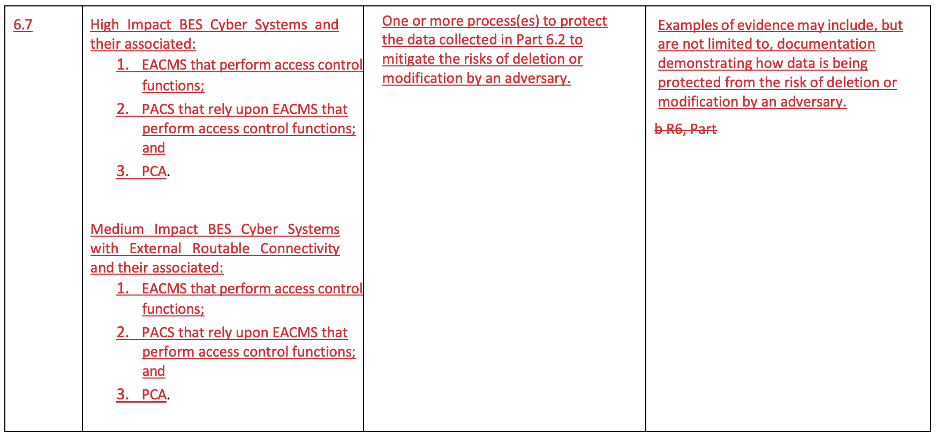
The seventh and final subrequirement (part 6.7, below) requires the entity to have “one or more process(es) to protect the data collected in Part 6.2 to mitigate the risks of deletion or modification by an adversary.” This one is unsurprising and makes sense. At least they didn’t go out with a crash.
CIP-007-X Part 6.7
The first draft of the INSM requirements is as low on ambition as they are high on ambiguity. While it takes a stab at meeting FERC’s directives, Requirement 6 tiptoes around the specifics, leaving industry insiders to navigate a labyrinth of vague directives and unbaked definitions. The draft sidesteps firm commitments on network monitoring coverage, edges around the murky concept of 'anomalous activities,' and casts a controversial net by possibly looping in external EACMS. It’s a mix of auditability challenges and interpretative loopholes that may leave entities grappling with more questions than answers.
For those seeking clarity, we have some great blog and podcast content:
Blog: Alexa, can you tell me when my grid is hacked?
Podcast: What to do about FERC's new INSM Order 887
Blog: What to do about FERC's new INSM Order 887
Blog: NERC Initiates Data Collection on INSM for Low Impact CIP Assets
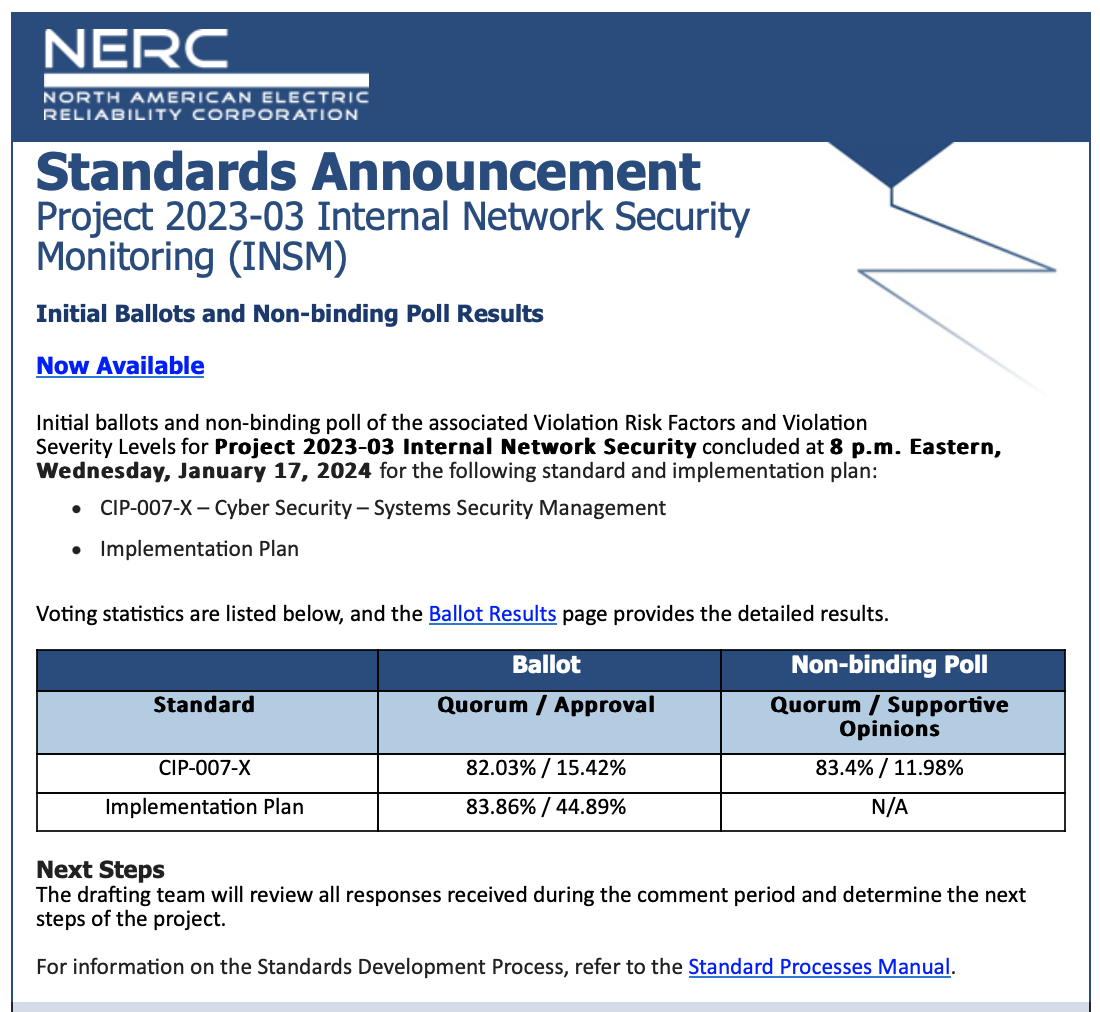
Update - January 18, 2024
The ballot body generated only 15.42% approval for this initial draft.